In today’s cybersecurity landscape, a particularly alarming threat has emerged that redefines our understanding of digital vulnerability. It’s a method of taking control of WhatsApp accounts that stands out for its technical simplicity and psychological effectiveness, as it doesn’t require the attacker to know or steal your password to succeed.
The Anatomy of the Deception: “I found your photo”
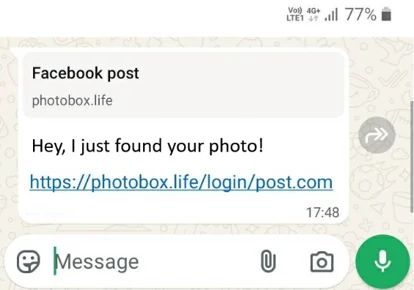
The attack begins in a seemingly harmless yet highly intriguing way. The user receives a message that employs a basic social engineering technique: curiosity or fear. With a phrase as simple as “I found your photo,” scammers manage to capture the victim’s immediate attention. This message is the bait for a process that allows a third party to silently and discreetly take complete control of the user’s account.
These types of tactics demonstrate that criminals are abandoning complex traditional hacking methods in favor of manipulations that exploit human behavior. Since no access key is needed, the average user may feel falsely secure, ignoring that the danger lies in linking the account to unauthorized devices.
Phone Number Vulnerability and Privacy
The magnitude of this risk is not isolated. Recently, a vulnerability in WhatsApp was documented, revealing the existence of billions of active accounts, which underscores a critical point: the importance of maintaining the privacy of your phone number. Your number is not just a means of contact, but a key to your digital identity that, if exposed, makes you a target for targeted attacks.
Sources emphasize that, in a world where personal data is easily leaked and sold, tools like BreachGuard are essential to protect your personal information and prevent it from being traded on illicit markets.
An Evolving Threat Ecosystem
This WhatsApp hijacking is just one piece of a much larger and more sophisticated fraud puzzle. Cybercriminals are constantly diversifying their methods:
- Fraudulent Text Messages (Smishing): From fake Amazon refunds to bogus DoorDash notifications or jury summonses, text messages have become a battleground for data theft.
- Job Scams: These messages are “exploding” on phones worldwide, becoming increasingly sophisticated in deceiving job seekers.
- Use of Artificial Intelligence: The advent of deepfakes and AI-powered ransomware is raising the bar for fraud sophistication, enabling much more convincing and difficult-to-detect attacks.
Comprehensive Defense and Protection Strategies
To combat these password-free threats, a proactive, multi-layered security approach is essential. Sources strongly recommend using advanced solutions like Avast Mobile Security, which helps keep scammers at bay and protects your personal information on mobile devices.
In addition to mobile protection, a comprehensive defense strategy should include:
- Browsing Security: Use secure browsers that protect against tracking and increase browsing speed.
- Identity Protection: Implement anti-tracking tools to mask your digital footprint and avoid targeted ads that could be used for scams.
- Connection Encryption: Using a VPN (SecureLine VPN) is essential for maintaining security when using public networks, where data can be more easily intercepted.
- Constant Updates: Keep all drivers and applications updated using automated tools to close technical security gaps.
For small and medium-sized businesses, protection extends to cloud security platforms and patch management, ensuring that not only individuals but also organizations are safeguarded against data loss and ransomware.
In short, digital security today is not just about having a strong password, but about being alert to unexpected messages and having an ecosystem of security, privacy, and performance applications that work together to protect us.


